Introduction
Before I explain why this tool was created, I would like to first start by explaining the basics and dependencies of the Microsoft Defender on a Windows Client.
Defender on Windows devices consists of 3 main components: Platform, Engine and the Signature. In order for Defender to use its full functionality, these components must be updated in regular intervals.
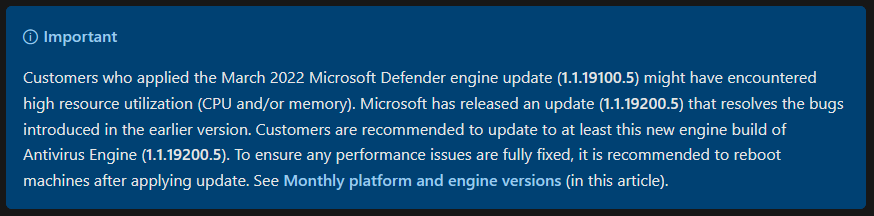
Especially the platform and the engine can lead to high CPU usage in older versions. Example for the engine version 1.1.19100.5:
- The Security Intelligence Updates include the signatures with virus and spyware definitions that are known to Microsoft and must be updated again and again.
- Platform Version is the current Defender Version.
- The Engine Version is the current version of the Defender scanning engine.
The platform and engine version are released monthly and are getting updates with your used Windows Update Service (e.g. WufB). You can find more infos about the KB here: Update for Microsoft Defender antimalware platform (KB4052623)
We will focus on the Security Intelligence Updates: Microsoft Defender Antivirus uses cloud-delivered protection and periodically downloads dynamic security intelligence updates to provide additional protection. Cloud-delivered protection is always on and requires an active connection to the Internet to function. Security intelligence updates occur on a scheduled cadence (configurable via policy). (Source)
Goal of this post
- Understanding the basics of Microsoft Defender for Endpoint.
- Check Defender Settings and Version.
- Create Defender Settings profile in Intune.
- Create your own GUI in Visual Studio and edit the Powershell Script.
- Web scraping the MDE Engine, Platform and Signature Version from Microsoft´s website.
Tools and Services used
- Microsoft Defender for Endpoint
- Microsoft Endpoint Manager
- Visual Studio 2022 (Community Version)
If you want to check out the tool and skip the explanations go to bottom of this post.
Defender for Endpoint Settings on the client
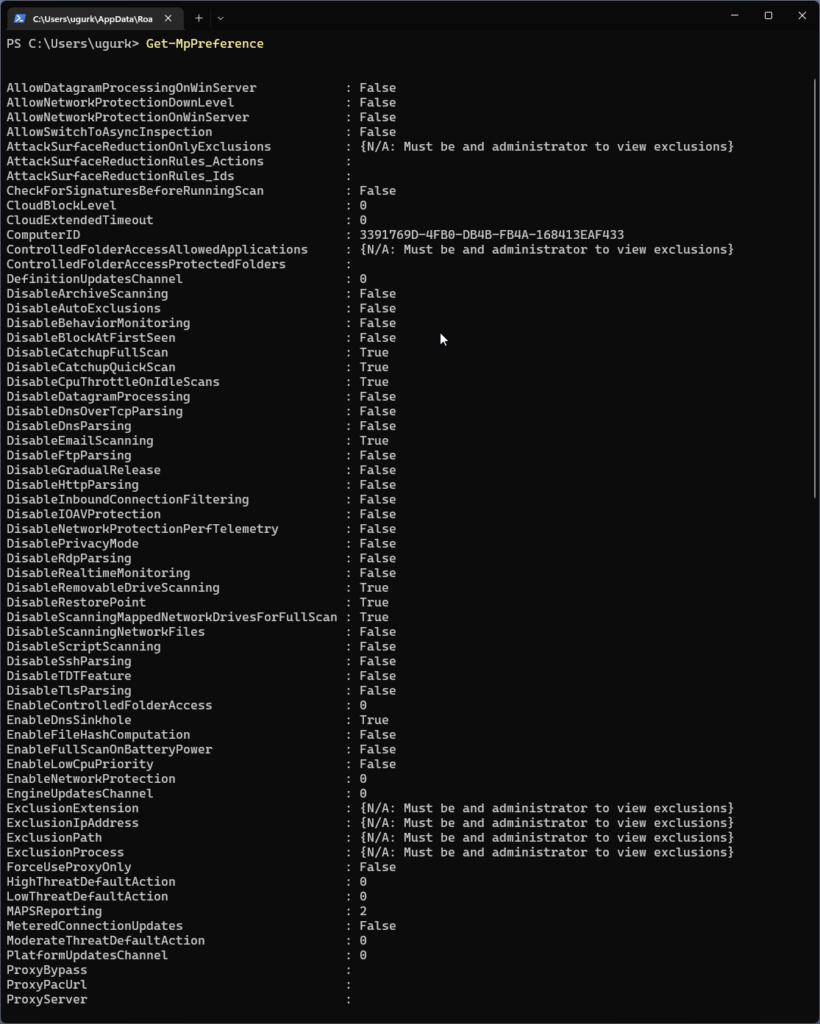
To see your current defender configuration start Powershell as a Admin and execute the following command:
Get-MpPreference
If you haven´t changed, enabled or disabled any settings then your configuration should look similar to this:
For the purpose of this blog post we just need to focus on the settings related to signatures. Let´s check signature related settings by executing following command in Powershell:
Get-MpPreference | select Signature*
This is the default config on my Windows 11 machine:
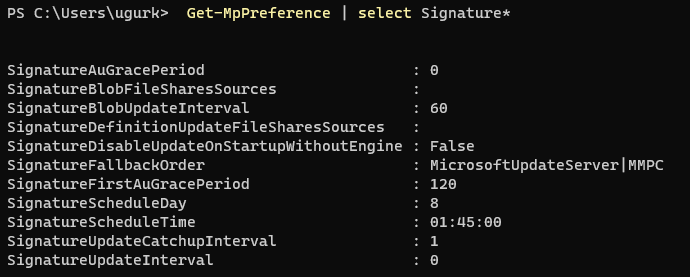
Do you see the Value “0” at the SignatureUpdateInterval? This means that the setting is not configured an therefore the signature update is done every 24 hours by default. Furthermore the Value “8” for SignatureScheduleDay is also a default setting and therefore the Windows Defender checks for definition updates by using a default frequency. This results in a signature update for every 8 hours.
Why would that even matter? Great question, let me try to show you why it could play a important role by answering another question:
How often are new Security Intelligence Updates released?
Anything related to changes, additions or updates to the defender signatures can be found here: Change Log
What I did was to research how often new signatures are being released. I wrote a little web scraper in Powershell and let it run in a Azure Automation Runbook for 5 Days. The web scraper checked the website from above every hour for changes and new versions. The results should not be that surprising for most of you: Microsoft released 18 signature updates. This is actually great, because signatures helps to protect our endpoints. Lets take a deeper look into the resulting numbers.
18 updates for 5 days means that there are 3-4 signature updates per day on average. That is good to know because we want our clients to have the newest signatures for better protection. Let´s have a look for the releases for a single day as an example. Take a look at the following table which shows the results:
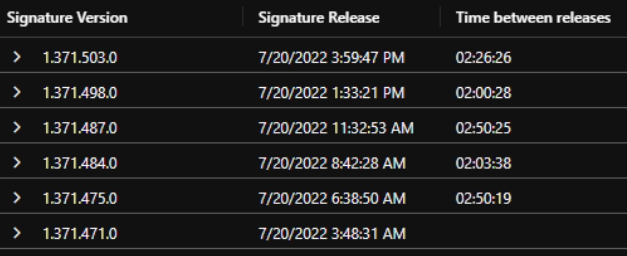
By piping the data from the web scraper to a Azure Log Analytics Workspace, I was able to query for the passed time between the releases to get a better understanding of how the releases are timed. As you can see there are about 2 to 3 hours between each new release.
Now, if you think again how often the windows clients (by default) search for signature updates (every 8 hours per Day) then we know that there is a high possibility that most of the devices wont have a up to date version of the Security Intelligence Update (= Signature) for the most time of the day.
Understanding that challenge, gives us the opportunity to search for a better way of handling the signature updates.
As we saw in one of the screenshots before, we have to change the value for SignatureUpdateInterval. The setting can be set via a GPO or in Intune. I will show you how to do it in Intune:
Signature Update Policy in Intune
Create a new policy in:
endpoint.microsoft.com -> Devices -> Windows -> Configuration Profiles -> Create Profile -> Platform: Windows 10 and later -> Profile Type Settings catalog
Click on next.
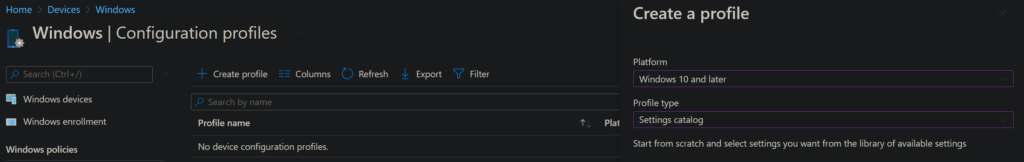
Give the profile a name and click on next. In the configuration profile, click on + Add settings and search for Signature Update Interval. Choose the only result showing up on the bottom left.
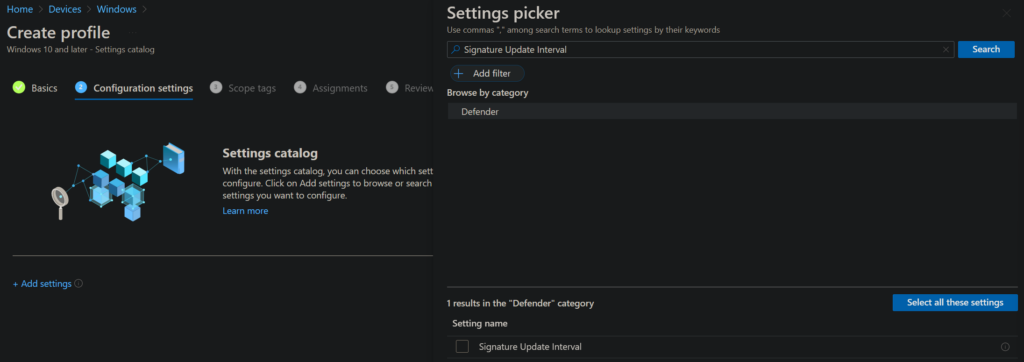
You can now enter a number. I will choose 2 hours for the reasons mentioned above.
Info: This Setting specifies the interval (in hours) that will be used to check for signatures, so instead of using the ScheduleDay and ScheduleTime the check for new signatures will be set according to the interval. A value of 0 means no check for new signatures, a value of 1 means to check every hour, a value of 2 means to check every two hours, and so on, up to a value of 24, which means to check every day. The default value is 8.
Click next, assign a device group and finally click on create.
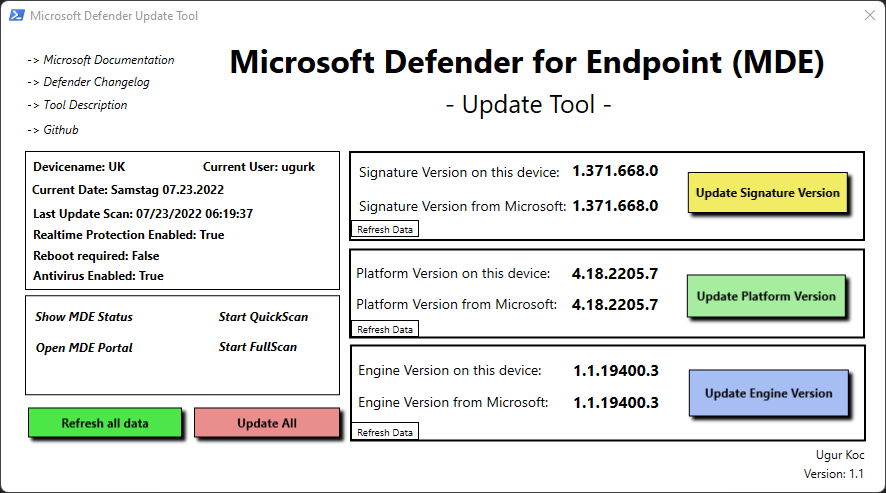
Update Tool with a GUI
To get a better overview of the defender settings as well as to trigger a update manually on the device, I created a little helper tool. The tool looks like this:
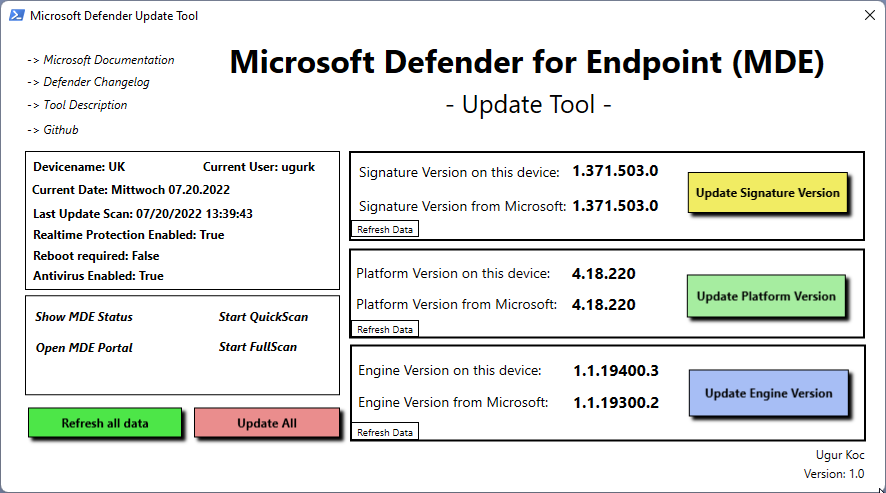
Update Tool – Features
- Show DeviceName and CurrentUser
- Show Current Date
- Show important Defender Settings:
- Last Update Scan
- Realtime Protection enabled
- Reboot required
- Antivirus enabled
- Update Signature Version
- Update Platform Version
- Update Engine Version
- Update all Versions of MDE
- Refresh all data inside the tool
The tool is basically a XAML formatted GUI with variables which are called in a Powershell Script.
This is how the XAML looks like in Visual Studio:
If you want to edit the GUI, then go and download the XAML file from my Github.
You have to make changes in the MainWindow.xaml file after opening the project in Visual Studio. You can not create or edit a WPF in Visual Studio Code. Just download the community Version of Visual Studio to play around.
The Powershell Script can be found here: Github
You can copy whats inside to a newly created file on your device and save it as a .ps1. You only need to execute the .ps1 to the test the tool. You can also make changes to the script as you like, add or remove functions. Just play with it 🙂
You can deploy the script to other devices with Intune if you want. You either package the .ps1 as a .intunewin Package and deploy the App or you deploy the Powershell Script. Let me show you how to deploy the .ps1 via Intune:
Go to:
endpoint.microsoft.com -> Devices -> Windows -> Powershell scripts -> +Add
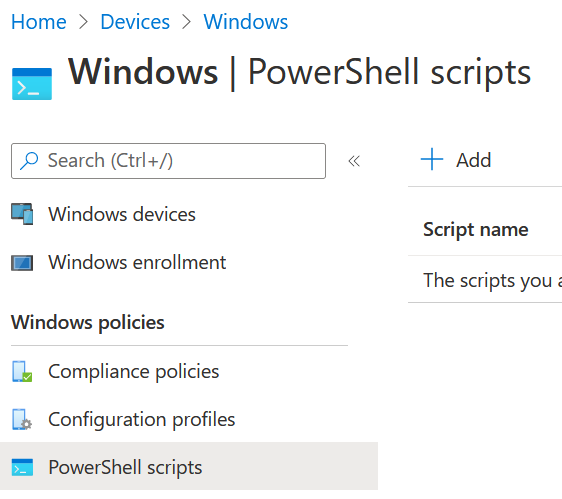
Give your Script Package a Name and click next.
Choose the .ps1 and don´t forget to switch to yes regarding the 64 bit Powershell Host:
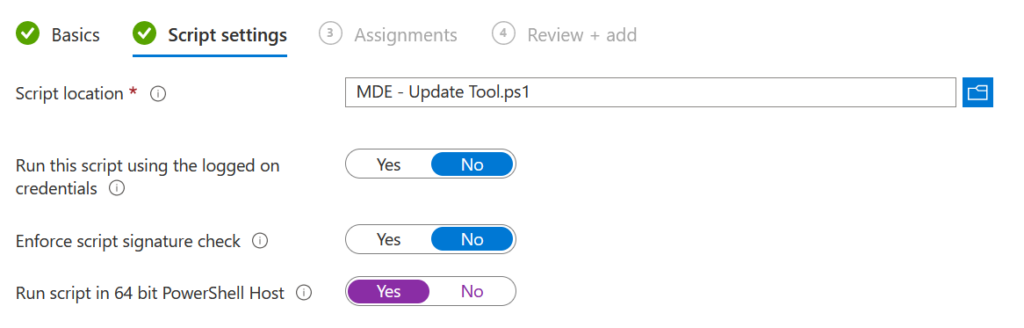
Click on next and assign the script to a device group. The result should look like this:
Conclusion
I hope that this blog post has helped you to have a better understanding of what dependencies the Microsoft defender has on your clients. I learned a lot by looking into how Microsoft releases Security intelligence updates and I hope that this tool will help you in that process.
Further information
Manage Microsoft Defender Antivirus updates and apply baselines
Update for Microsoft Defender antimalware platform (KB4052623)

1 thought on “Microsoft Defender for Endpoint (MDE) – Update Tool”
Comments are closed.