It’s Tuesday the 17th of September – a frosty morning. I wake up early, ready to start the day. The smell of my Americano with oat milk fills the air as I sip slowly, preparing for my first meeting. The day is off to a good start. Naturally, I check Intune to see how many people have already installed MacOS Sequoia, which was only released to the public yesterday.
Before I can even finish my coffee, a ping on Teams interrupts my moment of calm: “I’m having issues opening websites in Safari,” a colleague reports.
Coffee in hand, I pause and then jump into action.
I open Edge, curious. A quick look at X and Reddit confirms it: I’m not alone. Users are reporting DNS errors, VPN connection issues, and a ton of other strange problems. There’s one common link – they’re all on macOS Sequoia. This was a serious problem, as users across different environments were experiencing similar connectivity issues.
Some might say these things happen with new upgrades. But here’s the thing: we tested macOS Sequoia long before its release. I, along with many others, had been testing since the early beta versions. For those unfamiliar, Apple offers a program called AppleSeed for IT admins and developers, allowing early access to upcoming OS builds. The purpose is clear – to ensure that infrastructure, networks, and applications can handle the upgrade smoothly.
Sequoia wasn’t just another update; it was a big leap, packed with exciting new features powered by Apple Intelligence. Enterprises were buzzing to deploy it. Day Zero Support is an appealing idea, especially when it can boost productivity and bring shiny new toys to the end-users. But this time, something went very wrong – it left users completely stranded.
Don’t get me wrong – I love Day Zero Support when it works. If the features are solid, it’s a win-win for everyone. But being part of the AppleSeed program means you’re supposed to give feedback. And this time, we did. There were reports during beta testing – Beta 5, in particular – that highlighted severe issues: internet connectivity dropping, third-party security software malfunctioning (likely due to network filter clashes), and VPN connections failing altogether.
Apple was aware of the issue but perhaps underestimated its extent or impact.
So, here’s where we stand. There’s still no official statement from Apple, and we’re left with questions.
What went wrong? Could it have been prevented? And most importantly – how do we avoid finding ourselves in this position again? Let’s try to break it down.
Before we dive into the details, here’s a quick recommendation: if you’re interested in learning more about managing macOS devices with Intune, I highly recommend visiting IntuneMacAdmins.com. It’s a great resource for IT admins working with macOS in enterprise environments.
Issue Identification
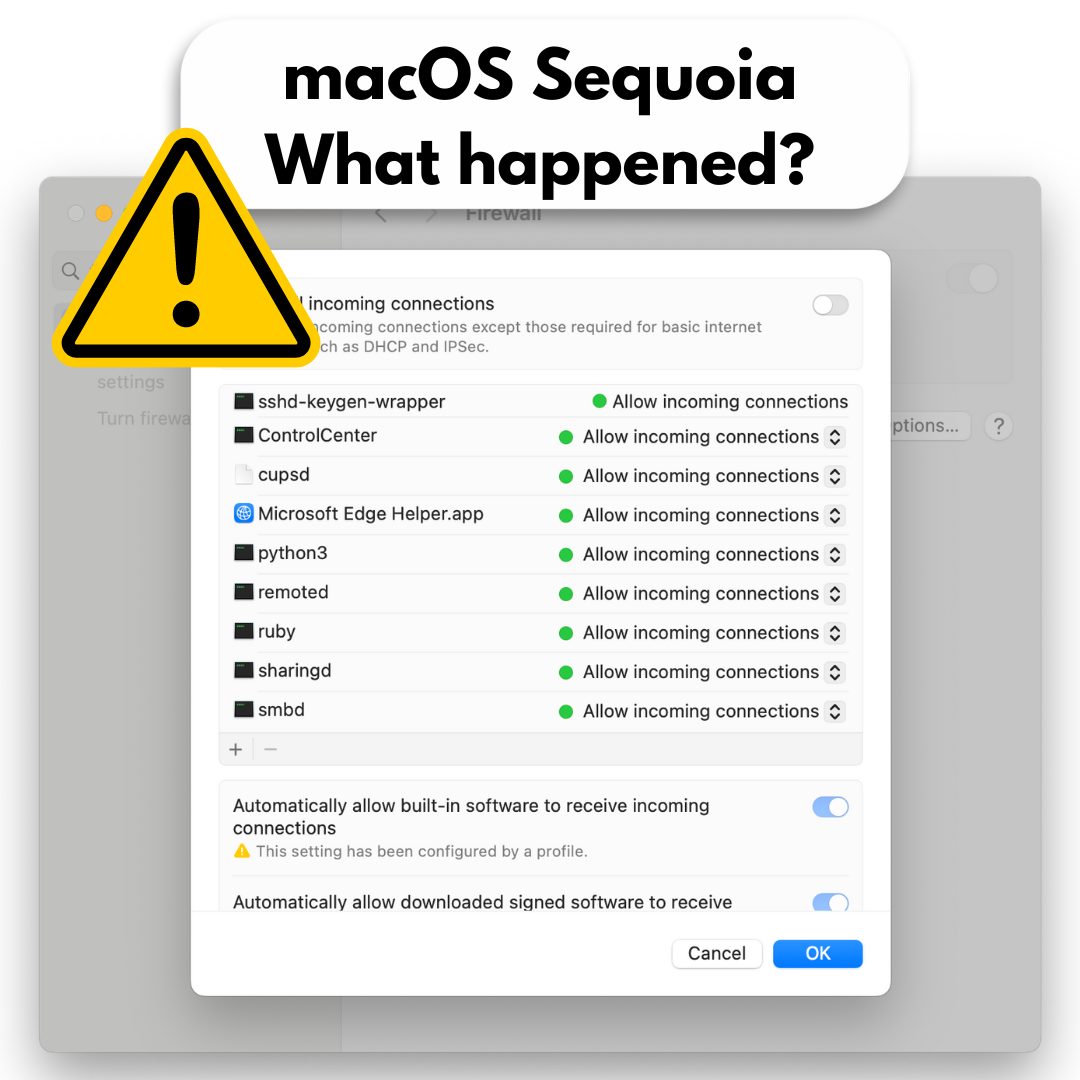
macOS Sequoia version 15.0 introduced significant challenges, particularly impacting VPN functionality and third-party security software. The root cause stemmed from changes to the built-in Application Firewall, specifically how it handles application settings within property files. These modifications led to widespread reports, including from our own users, on platforms like X and Reddit. The issue involved the firewall automatically blocking incoming internet connections for certain applications, even after users manually adjusted their settings. Upon reboot, these settings would revert, causing inconsistent connectivity or complete connection drops when the firewall was enabled.
A quick note – similar issues occurred with macOS 13 and 14, but in those cases, only the beta versions were impacted, not the full public releases of the respective minor and major versions.
Challenges During Sequoia’s Beta Testing Phase
Apple provides beta versions to developers and IT administrators through a private preview, allowing them to validate the compatibility of their environments and applications. Participation in the Apple Seed Program grants early access to these builds. Major VPN and security software vendors had access to the macOS 15.0 beta, providing ample time to ensure compatibility with the new operating system.
Despite extensive testing, including our own, connectivity issues began surfacing during Beta 5. Reports on platforms like X, Reddit, and feedback via the AppleSeed Program highlighted these problems. However, it appears that Apple was unable to fully diagnose or address the problem before the final release. It’s likely the fixed release schedule limited their ability to resolve these issues prior to launch.
Impact of the Issue
Many users were eager to upgrade to macOS 15.0 to explore Apple’s new AI-driven features. AI – Apple Intelligence – is the buzzword here, but it’s worth noting that these features are being introduced with macOS 15.1, currently available in beta. However, after Sequoia was installed, sporadic connectivity issues began to emerge across a variety of devices and applications. These issues were inconsistent, sometimes resolving without intervention, and varied depending on the software in use. For example, some users experienced disruptions with CrowdStrike, while others faced difficulties with Microsoft Teams.
The issue was made worse by Apple’s lack of communication, affecting both personal and business devices worldwide. In contrast, other vendors were more transparent, quickly acknowledging compatibility issues with macOS 15.0 and providing workarounds to mitigate the impact.
Solution to the Issue
Identifying the root cause was challenging, but the solution was relatively straightforward. A temporary workaround involved either disabling the Application Firewall or manually unblocking specific applications affected by connectivity issues. However, this approach posed security risks, particularly in enterprise environments where safeguarding incoming traffic is critical.
Although we were able to apply this workaround successfully on some devices, a complete solution was achieved only when Apple released macOS 15.0.1, approximately three weeks after the initial launch of version 15.0.
For a detailed overview of updates in macOS Sequoia 15.0 and 15.0.1, visit Apple’s support page.
Into the Future
I’m a strong advocate of “Day Zero” support, as mentioned earlier. Rolling out highly anticipated features like Apple Intelligence and new management capabilities with Declarative Device Management for macOS 15 is welcomed by end users. It also showcases the enterprise’s and IT administrators’ ability to swiftly and effectively enable new technologies.
However, while testing before a major update is essential, as discussed earlier, there is no fail-safe method. Even if you rigorously test the beta versions, it’s equally important to validate the public release as well. In fact, I recommend going one step further – wait for the first minor update before upgrading to macOS 15. With macOS 15.1 expected in November, consider holding off your upgrade from macOS Sonoma to Sequoia until then.
Deploying updates in multiple waves is a wise strategy. This staged approach allows you to pause the rollout if any issues arise, minimizing the impact on your users.
Conclusion
The release of macOS Sequoia 15.0 highlighted the complexities and challenges of adopting new software, especially when key features and security settings undergo significant changes. While Day Zero support allows organizations to stay ahead of the curve, it also brings risks when unforeseen issues arise, as we saw with the firewall and connectivity problems.
The key takeaway is clear: thorough testing and caution are essential, even when new features promise to revolutionize user experience. By waiting for subsequent updates, such as the expected 15.1 release, and deploying upgrades in staggered phases, organizations can safeguard against widespread disruptions.
Ultimately, the goal is to balance innovation with stability, ensuring that new technology brings both excitement and the reliability users and IT admins need. With careful planning, we can continue to embrace the future without sacrificing the seamless functionality our environments require.