Introduction
IT administrators constantly juggle maintaining security and ensuring smooth system operations. A critical part of this task is regularly applying software updates and patches. Typically, Windows updates require system reboots, disrupting user workflow and productivity. To address this challenge, Microsoft introduced Hotpatch—a feature aimed at significantly reducing reboot disruptions. This post provides IT admins with a clear overview of Windows Hotpatch, explains how it works, and guides on deploying it using Microsoft Intune.
The Problem – The Realities of Patching
Traditional Windows patching is essential but often frustrating. Forced reboots interrupt users, causing downtime and productivity loss. Scheduling these reboots is also tricky, particularly for globally operating companies or those needing continuous uptime. Monthly security updates traditionally require multiple reboots each year, affecting user satisfaction and overall efficiency. Moreover, the inconvenience leads users to delay updates, potentially exposing systems to vulnerabilities.
The Solution – Introducing Hotpatch
Microsoft developed Hotpatch specifically for Windows 11 Enterprise (version 24H2) to apply security updates without a reboot. Hotpatch updates security patches directly into active processes in memory, eliminating the need to reboot and minimizing disruption. This results in fewer interruptions, quicker deployment of security fixes, and easier update management for IT teams.
How Hotpatch Works
Hotpatch applies patches directly into the running system’s memory rather than replacing files on disk. Devices receive a comprehensive cumulative update once per quarter (in January, April, July, and October) that does require a reboot. Between these quarters, monthly Hotpatch updates deliver critical security fixes without requiring a restart. Devices receiving Hotpatch have distinct identifiers (KB numbers) and OS version numbers, simplifying management for IT teams.
Prerequisites for Hotpatch
To use Hotpatch, IT environments must meet specific requirements:
- OS: Windows 11 Enterprise version 24H2 or later
- Licensing: Windows 11 Enterprise E3/E5/F3, Education A3/A5, or Windows 365 Enterprise subscription
- CPU: x64 architecture
- Security: Virtualization-Based Security (VBS) enabled
- Baseline: Latest quarterly update installed
- Management: Microsoft Intune
- Arm64 Devices (currently in preview): Requires additional registry configuration or CSP adjustment, followed by a reboot.
Hotpatch and Microsoft Intune
Hotpatch integrates smoothly with Microsoft Intune, allowing easy management through familiar Windows quality update policies. Administrators can enable Hotpatch by adjusting Intune settings, ensuring seamless integration into existing workflows. Additionally, organizations using Windows Autopatch benefit from automated deployment based on established deployment rings, further reducing administrative overhead.
Implementing Hotpatch in Intune
Follow these steps to enable Hotpatch:
- Sign into the Microsoft Intune admin center.
- Navigate to Devices > Windows updates.
- Under the Quality updates tab, select + Create > Windows quality update policy (preview).
- Enter a clear policy name and description.
- Configure the policy settings:
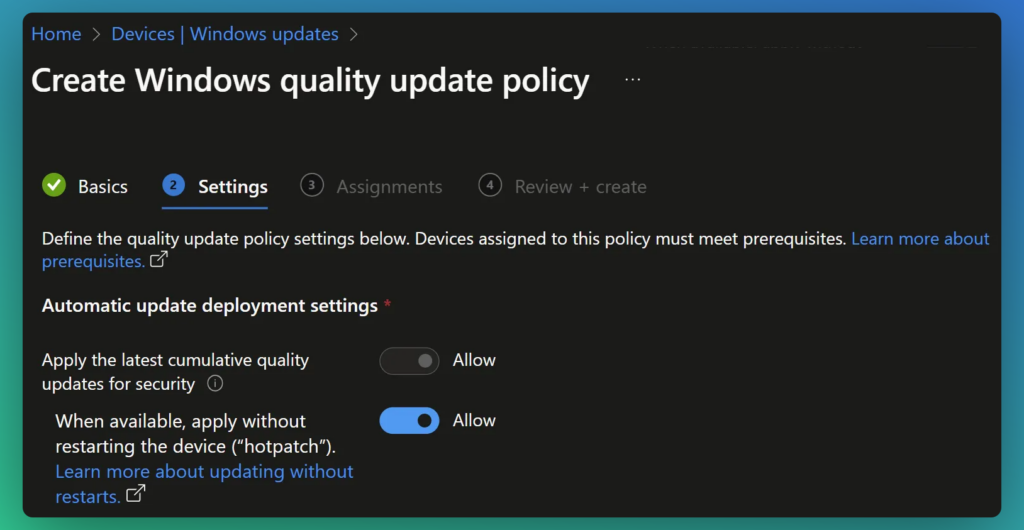
- Allow cumulative quality updates for security.
- Allow applying updates without restarting (Hotpatching).
- Assign this policy to appropriate Entra ID groups.
- Review and confirm the settings before creating the policy.
You can verify successful deployment in device update settings under Configured update policies, confirming Hotpatch is enabled.
Benefits of Using Hotpatch
- Reduced downtime by decreasing mandatory reboots from approximately twelve per year to four.
- Faster deployment of focused security updates, increasing overall security.
- Enhanced compliance due to fewer interruptions and timely patching.
- Immediate protection as security updates take effect instantly without reboot.
Limitations and Considerations:
While advantageous, Hotpatch currently supports only security updates, excluding .NET framework and non-security updates, which still require reboots. Quarterly reboots remain necessary for baseline updates. Arm64 support is still in public preview, requiring careful implementation. IT admins should also be aware of potential reporting discrepancies in security tools and the lack of automatic rollback for problematic updates, necessitating manual intervention if issues occur.
Conclusion
Windows Hotpatch significantly enhances Windows update management by reducing system reboots and improving productivity and security. IT admins are encouraged to assess Hotpatch’s prerequisites and consider integrating it into their environments. By providing feedback and staying informed about ongoing improvements, administrators can fully leverage Hotpatch to achieve fewer disruptions and a more secure IT infrastructure.
