
Homebrew is a very popular tool for MacOS (and Linux) Users to install applications in the user context ignoring the local privileges and ignoring application and patch management. I am sharing my solution/workaround to address the challenges of users using Homebrew on Intune managed MacOS Devices. Shall we begin?
What is Homebrew for MacOS?
Homebrew for MacOS makes your life easier by speeding up and simplifying software installation. It’s great for accessing a wide range of software packages through its main repository. Plus, with the ‘cask’ extension, you get even more software options, including binary apps. If you’re good with command-line tasks, you’ll find Homebrew super user-friendly.
To install software using Homebrew on MacOS, you would typically use a command in the Terminal that follows this format:
brew install [package-name]For instance, if you wanted to install the package “wget” you would enter the following command in your Terminal:
brew install wgetImplications of Homebrew:
When software is installed using Homebrew on MacOS, it is typically installed in the user context, not the system context. This means that the software and its related files are installed in locations that are accessible and modifiable by the user, without needing system-level (root) permissions.
Specifically, Homebrew installs software into directories like /usr/local/bin for Intel-based Macs or /opt/homebrew for Apple Silicon Macs.
No Root Privileges Required: Since the installations are done in user space, there’s generally no need for root or administrator privileges to install or manage the software. This enhances security by minimizing the risk of unauthorized system modifications.
Letting users install software on their own could lead to a conflict with your patch management and vurlnerability reportings.
I have looked into the best way to block Homebrew but could not find a definit solution. Instead I have worked on creating multiple layered blockages that will hinder a normal user to run install or run homebrew on a MacOS.
What happens after the script runs?
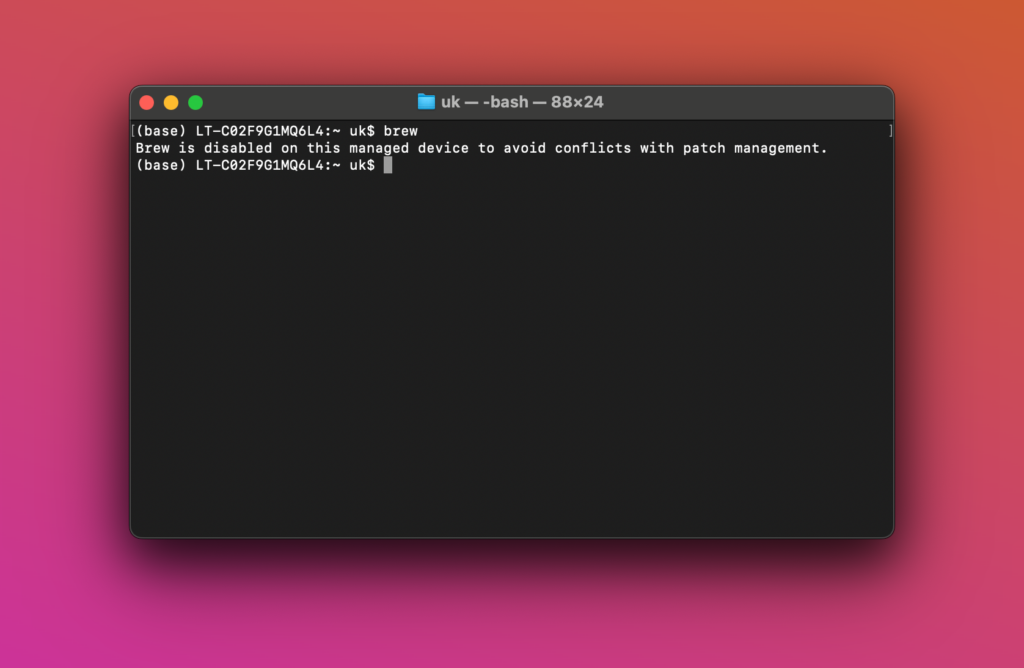
I made the below screenshot to show that the installation of Homebrew is not that easy anymore:
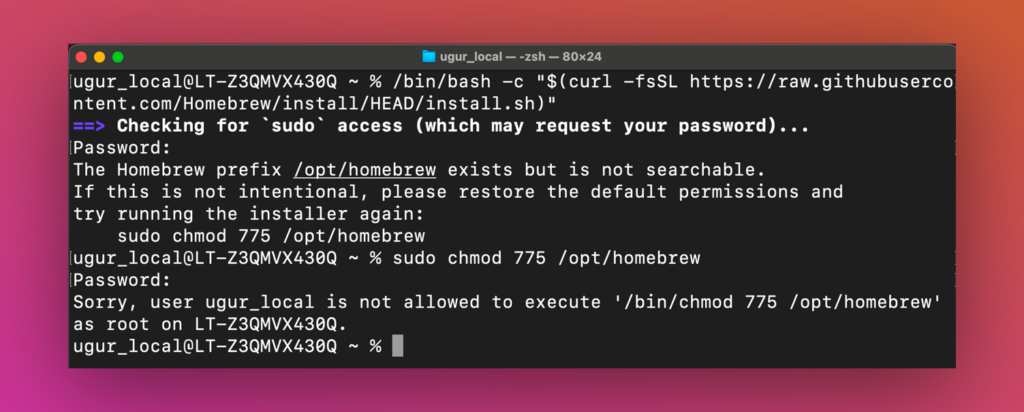
If the user has Homebrew already installed (the script also will uninstall it), changing the permissions of the installation folder causes the following “Permission denied”:
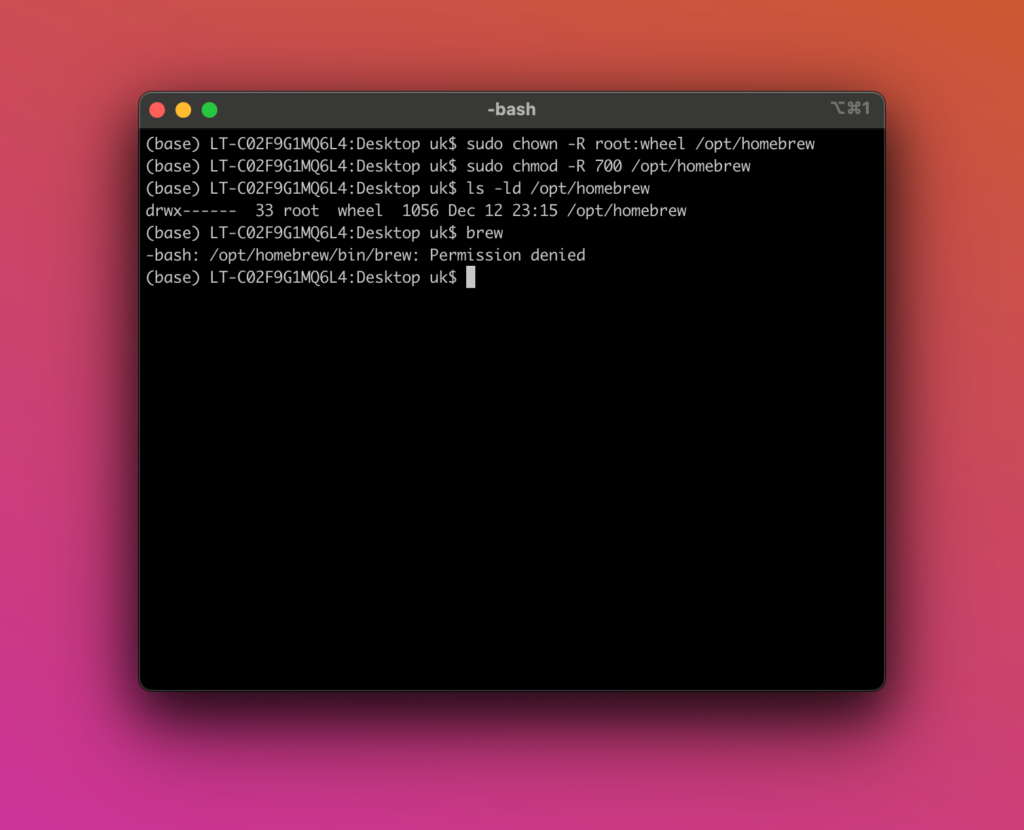
If the user manages to run the brew command it will show the alias but not execute brew:
I have also tried using a Device Restriction policy restricing Homebrew but I could not make it work. Maybe others will discover better ways to block it.
Script Overview
Lets go over what the script does by looking at every step and describe the expected behavior.
Dynamic Path Setting
The script intelligently sets the Homebrew installation path based on the CPU type. It identifies whether the processor is an Apple Silicon or Intel and sets the path to /opt/homebrew or /usr/local respectively. This ensures compatibility across different Mac models.
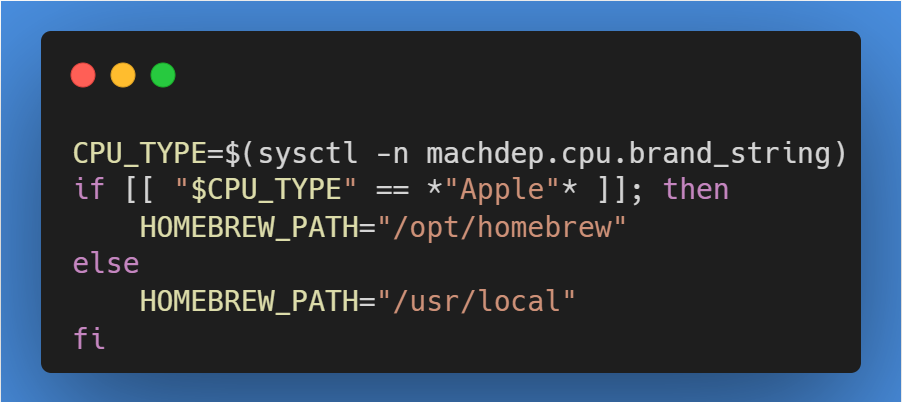
Directory Ownership and Permission Modification
If the Homebrew directory exists, the script changes its ownership to root and restricts access permissions, effectively limiting the ability of normal users to modify the Homebrew installation. If the directory doesn’t exist, it is created with these restricted permissions.
Alias Implementation
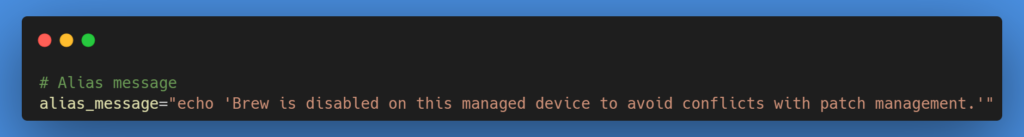
To prevent the execution of Homebrew, the script sets an alias for the brew command. This alias triggers a message indicating that Homebrew is disabled, effectively blocking its use.
Profile Modification
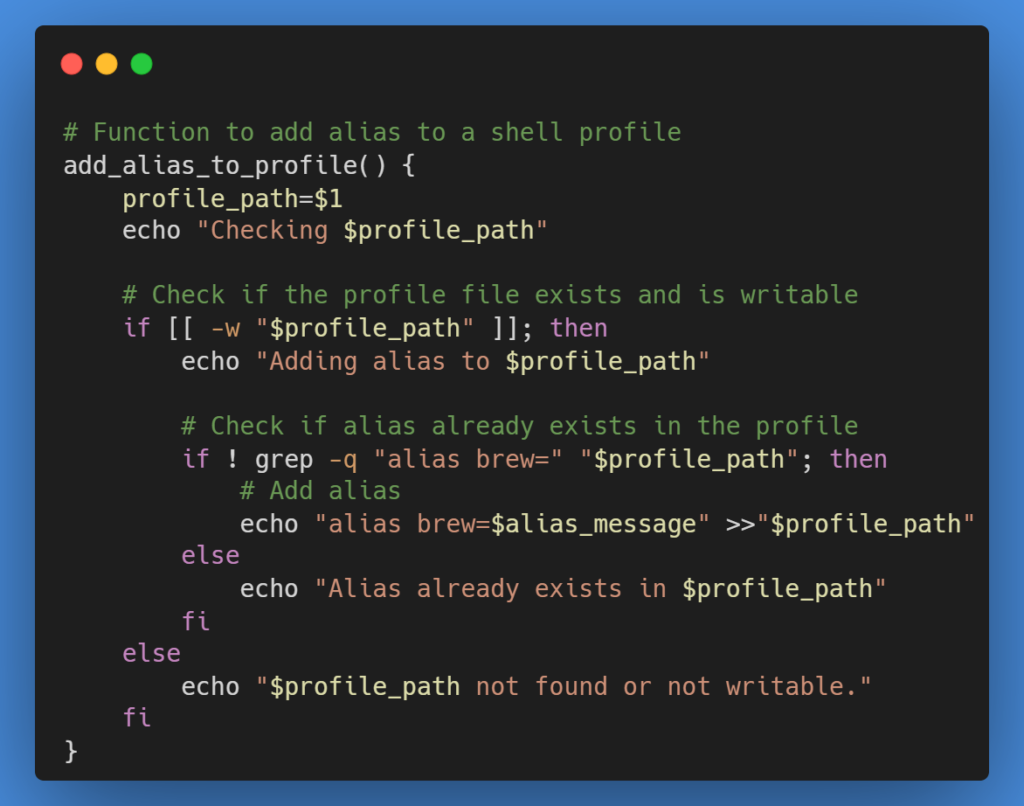
The script adds the above-mentioned alias to commonly used shell profiles (.bash_profile, .bashrc, .zshrc). This ensures the alias is active across different shell environments.
Sudoers File Restriction
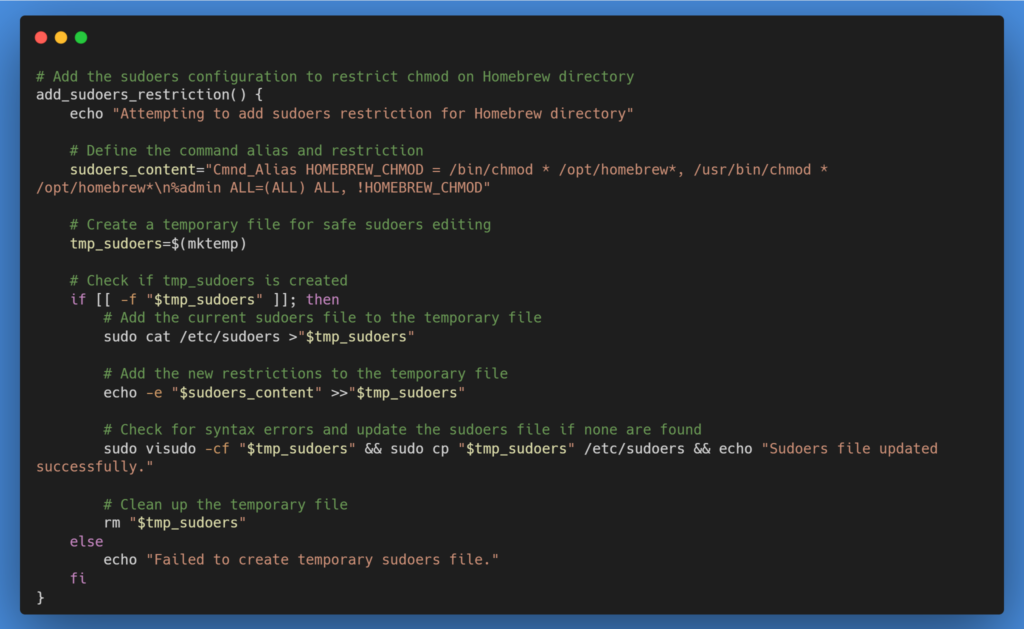
An important layer of this approach involves editing the sudoers file to restrict the use of chmod on the Homebrew directory. This step adds an additional layer of security, preventing administrative users from easily changing permissions back to a state where Homebrew could be used.
Temporary Sudoers File for Safe Editing
The script creates a temporary sudoers file to ensure that any changes made are syntax-error-free before they are applied to the actual sudoers file. This step is crucial for maintaining system stability and security.
Download the script
Intune/MacOS/Block_HomeBrew.sh at main · ugurkocde/Intune (github.com)
Deploy with Intune
You can deploy the shell script with Intune. I always recommend you to first test this script on a test device.
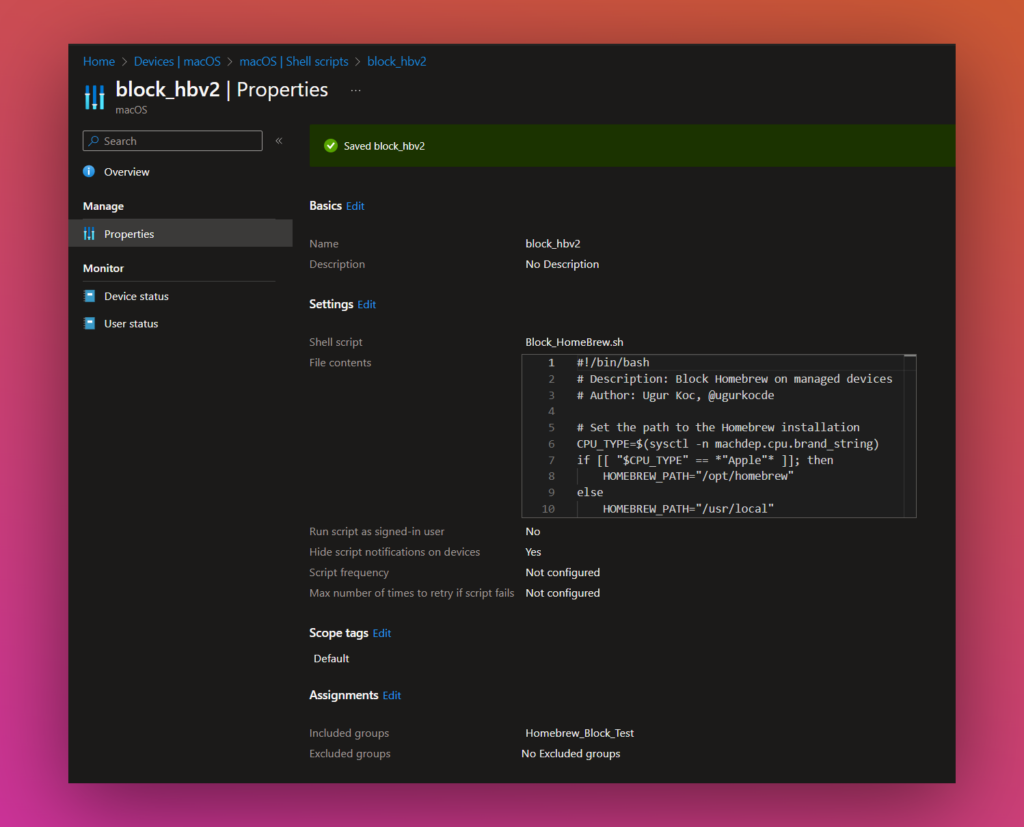
Go to Shell Scripts in Intune and click on “+Add” and edit the settings as well as upload the script you have downloaded before.
Here is a screenshot of my shell script settings in Intune:
After the deployment you should see results in the “Device Status”:
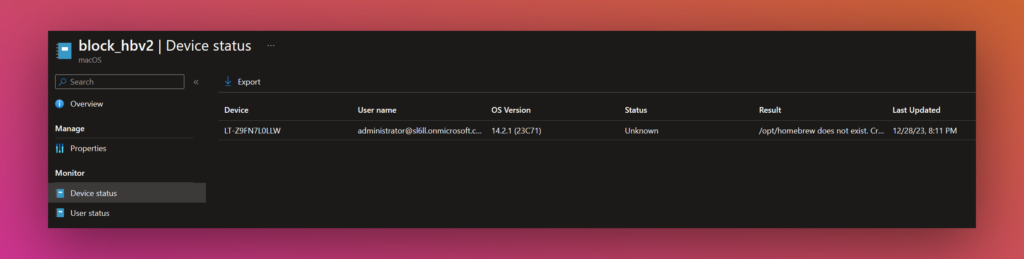
The Output is in the Results column.
Conclusion:
I hope that this approach gave you an idea of how to block Homebrew on MacOS. I am open for every kind of Feedback and Improvements to the script. Feel free to create an Issue or PR on GitHub and you can contact me on X @ugurkocde.
Disclaimer:
I am not responsible for any errors or omissions, or for the results obtained from the use of this information. The use of the script and information is at your own risk. It is advised to test the script in a controlled environment before deploying it in a production scenario.
1 thought on “Block Homebrew on MacOS with Intune”
Comments are closed.